Overview
G1 Galahad mode allows visualizing of virtual steps of the cutting process of stone. G1 Galahad mode helps cutter to cut facets correctly by visual control of facet shape and difference values of slope, azimuth, distance between plan and current model.
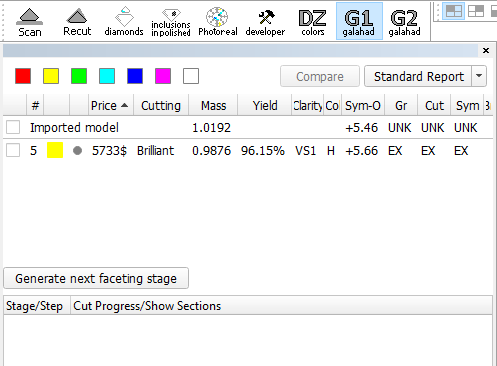
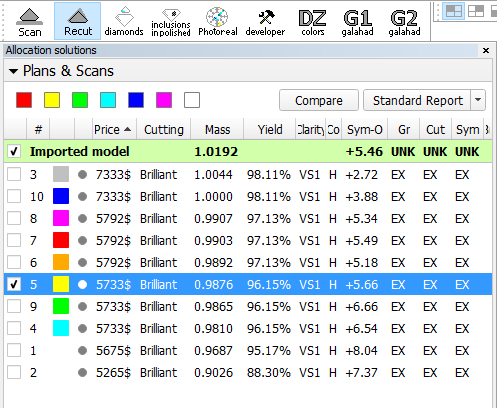
G1 mode shows the main scan and active solution (target plan) from Recut mode:
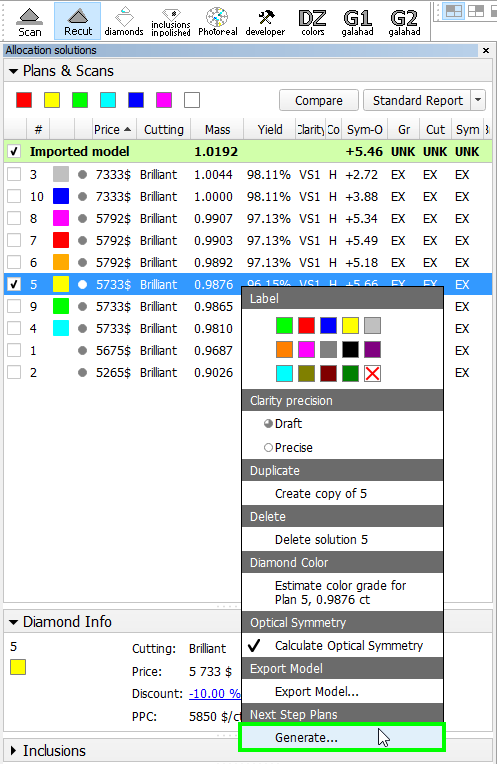
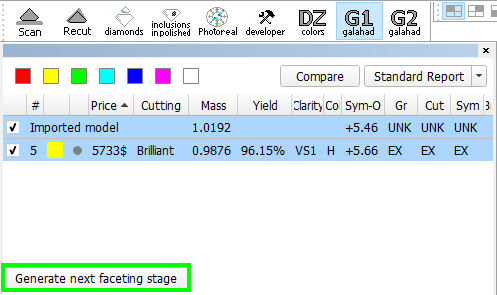
"G1 Galahad" mode "Recut" mode - To get steps is required either right-click on the selected solution, in the context menu select "Generate..." under "Next Step Plans" group, from Recut mode or click button "Generate next faceting stage" from G1 mode.
OR
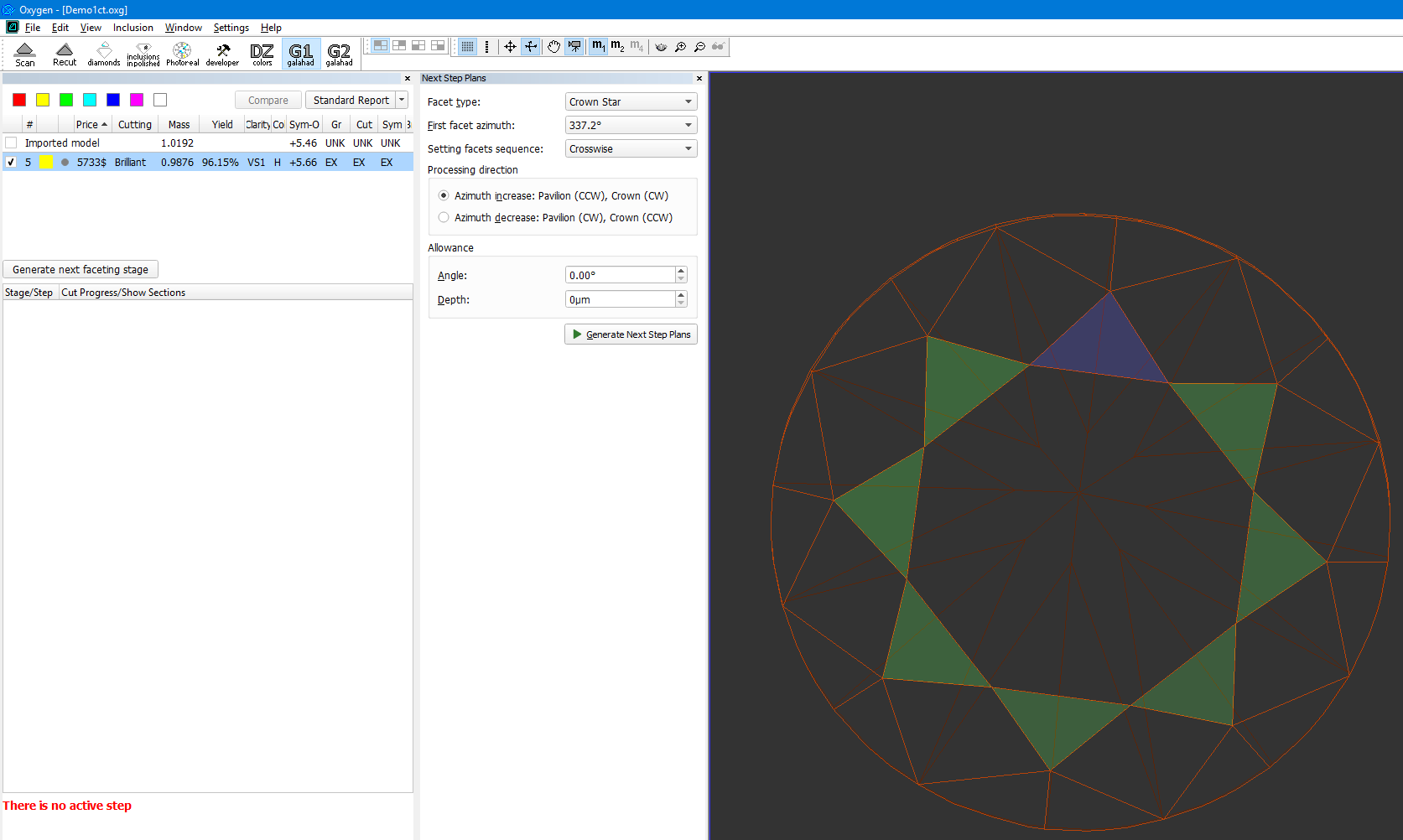
- "Next Step Plans" panel appears, selection of facet type is highlighted by dark green in the scene and first facet of selected type is highlighted by violet.
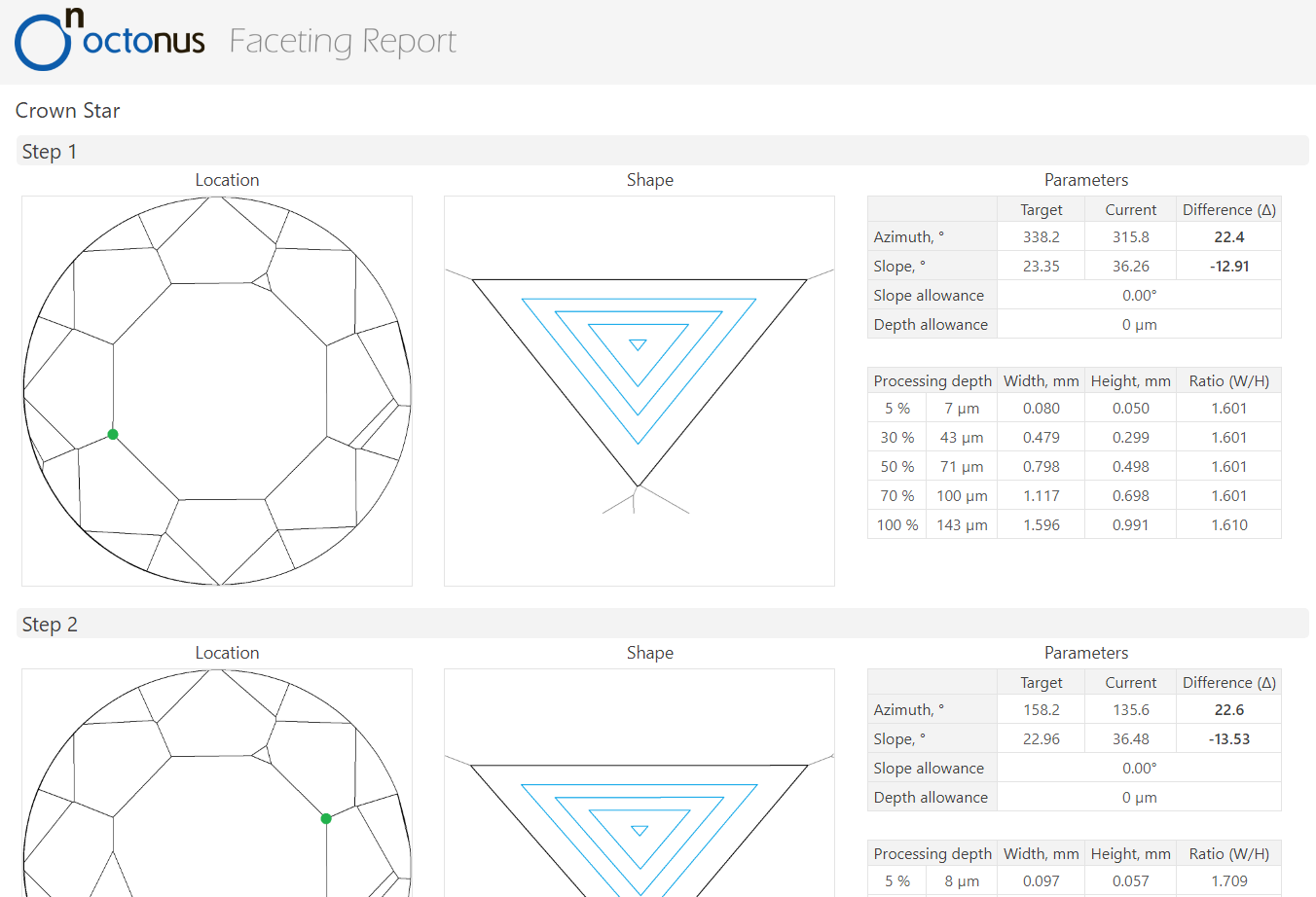
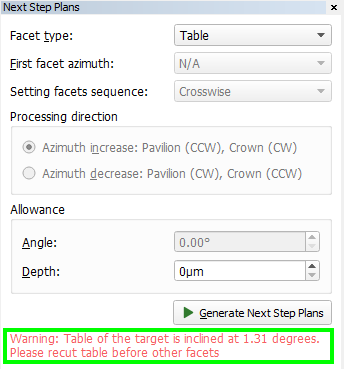
In the panel "Next Step Plans" operator can configure polishing stage parameters, in the scene operator can select facet type and first facet by simple click. - After configuring the parameters, click "Generate Next Step Plans" button, Faceting Report is generated and opened in the default system browser automatically.
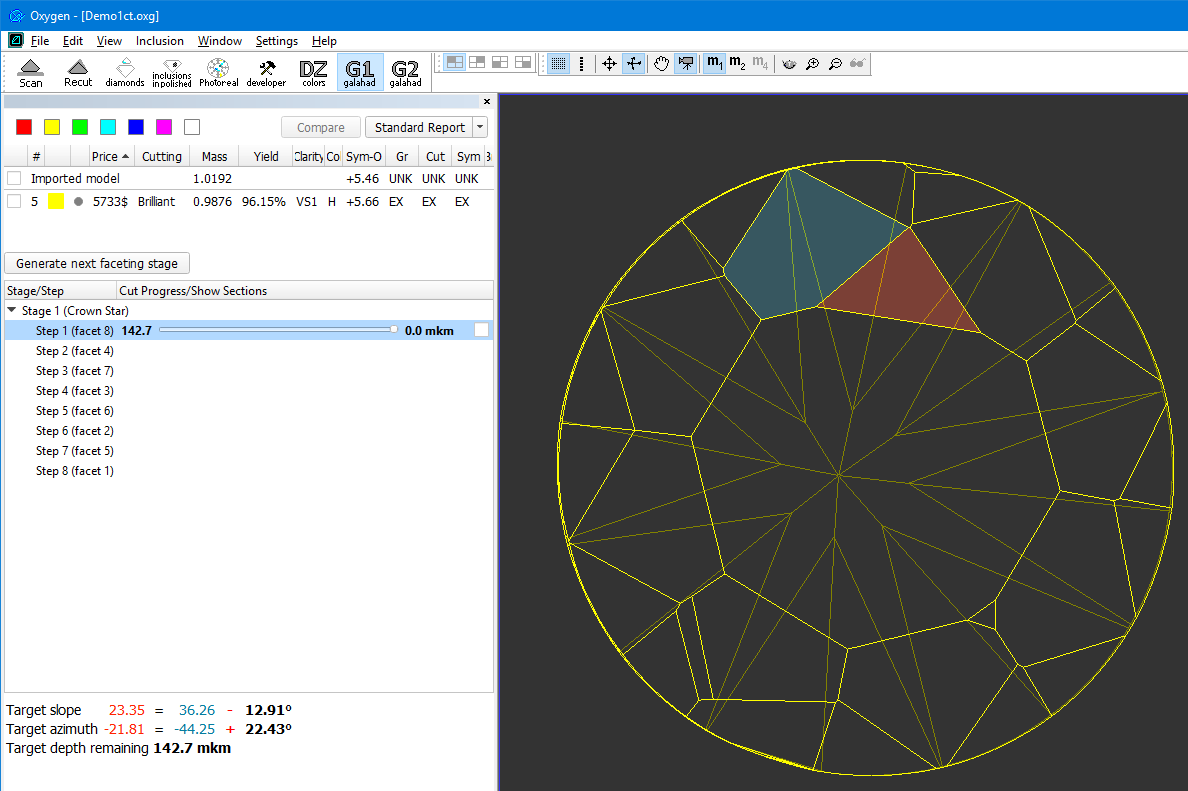
- To view the generated faceting stage, switch back to Helium Polish Oxygen software and check table in "Plans&Scans" with stages and steps of cutting:
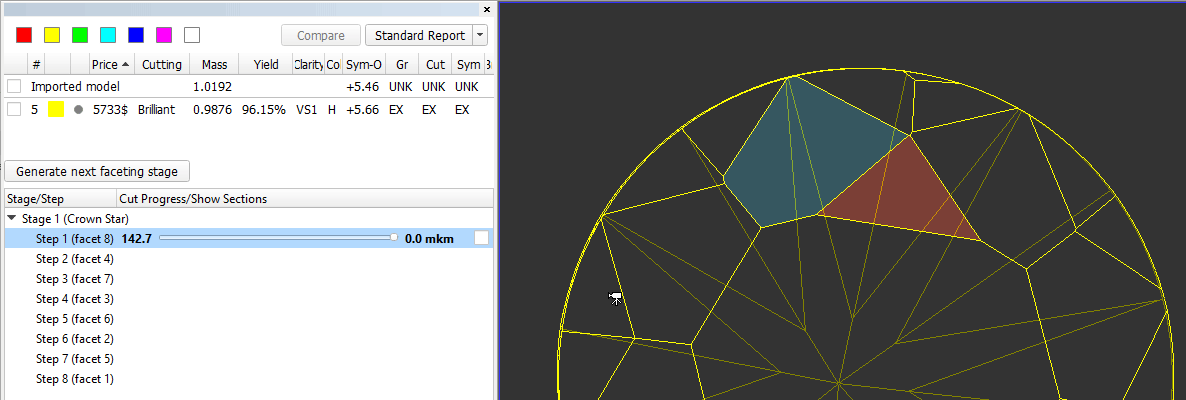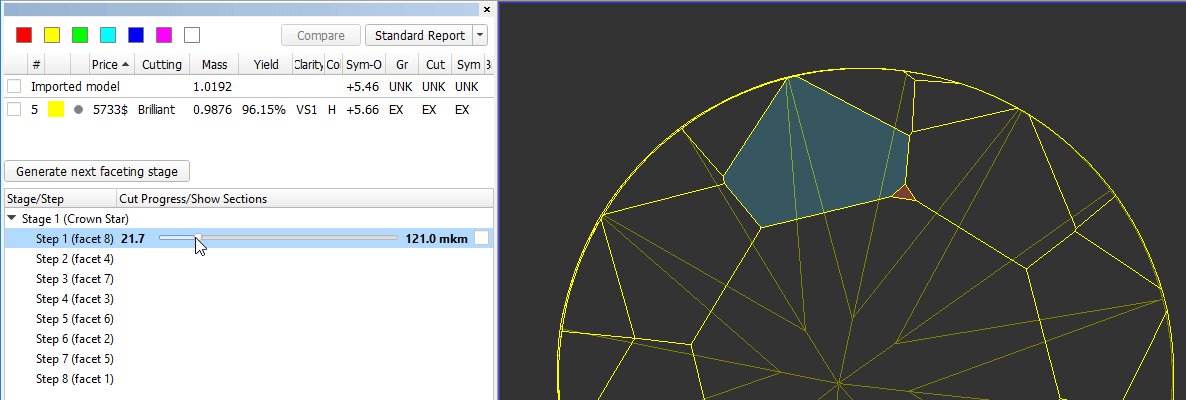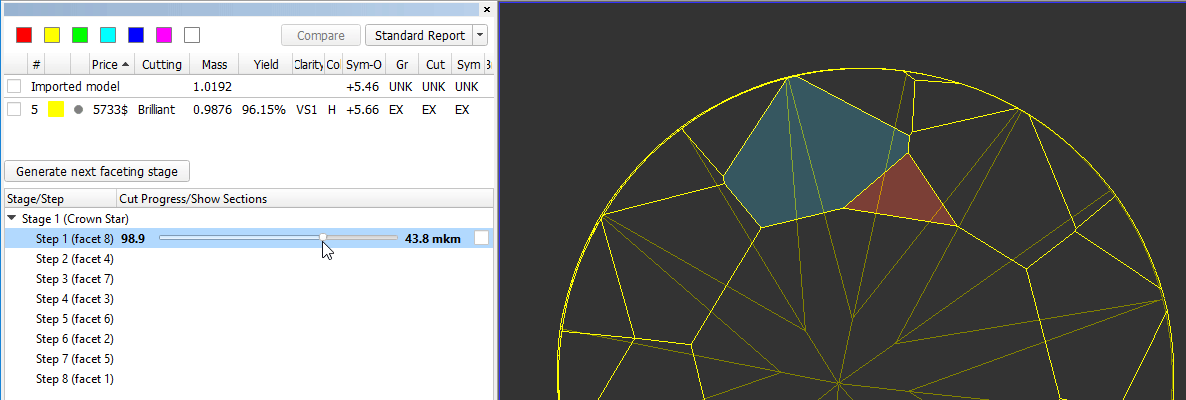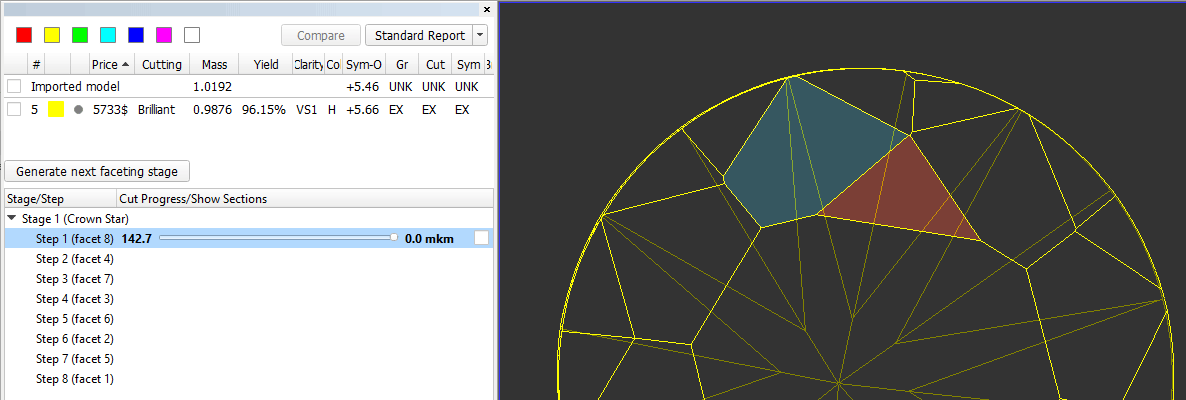
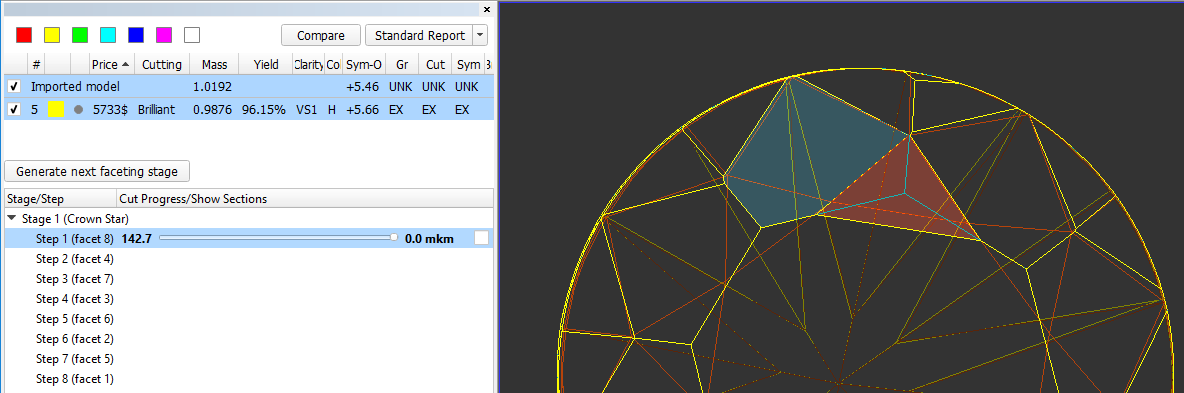
In the Scene operator can see yellow model which correspond to current stage/current step. Current facet under cutting is highlighted by color. Facet, highlighted by color, is the nearest facet to current.
In left panel with stages/steps operator can see slider which by default is the end of scale for each step. Position of slider displays current level of cutting and correspond to model on the right.
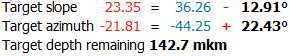
There are values on in the beginning and in the end of scale - they mean distance of cutting which is already passed for model on the right and distance which is left till end.
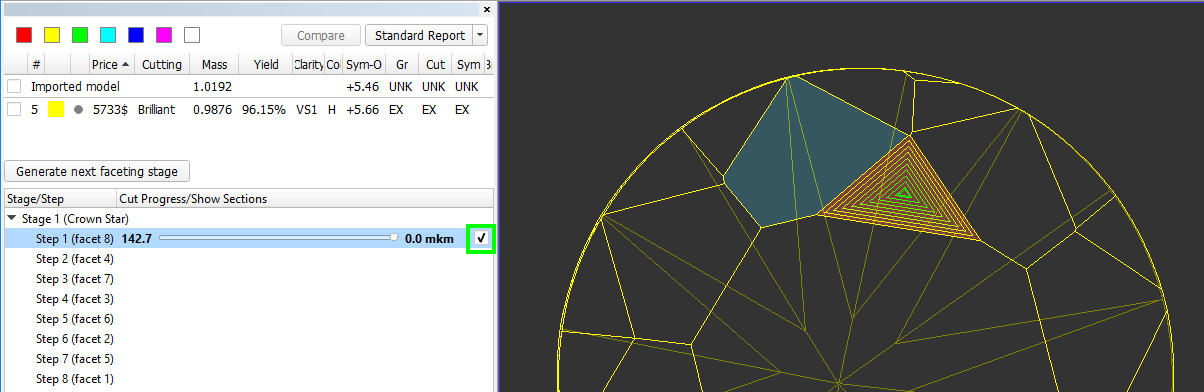
Checking box shows levels of cutting:
Information under the stages/step shows slope angles and azimuth angles of final plan model and current step model (yellow) and difference between them. Also target depth of cutting is shown: - Operator can check boxes on the left top table and see in scene plan (red) and original (blue) model:
- After cutting of Stage 1 facets, operator has to press button "Generate next faceting stage" and proceed with next facet group.
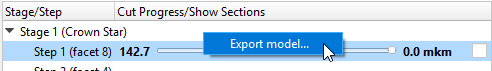
- Right click on step item allows to export the current model model to .mme file:
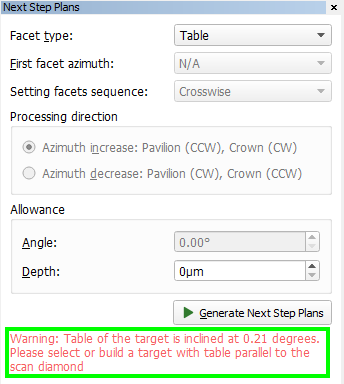
Note: If table of plan is inclined more than 1 degree then alert message to recut table will be shown in panel Next Step Plans . If table of plan is inclined more than 0.1 degree but less then 1 degree then alert message to select another plan will be shown in panel Next Step Plans
Operations with Stages and Steps
You can perform different operations related to stages and steps.
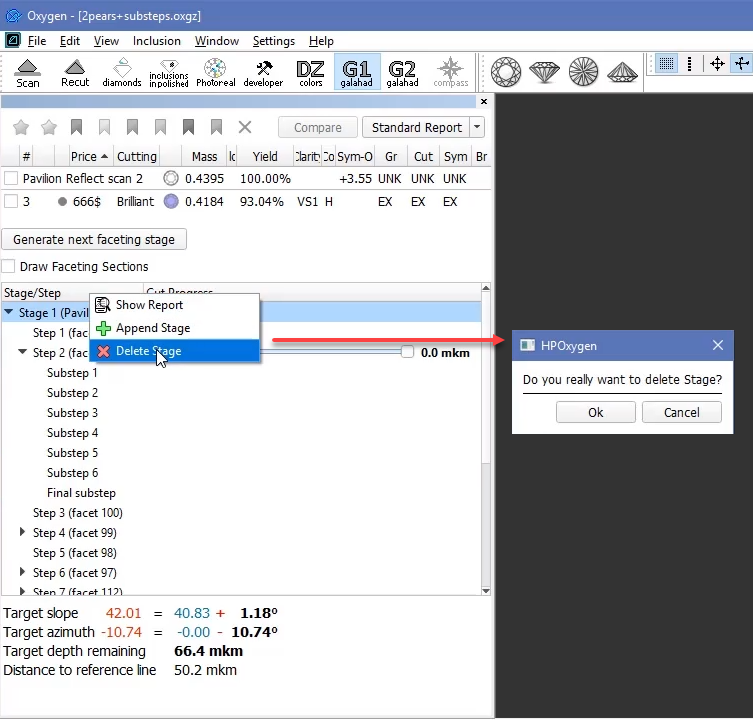
Deleting Stages
To delete the stage:
- In the G1 Galahad mode, on the left panel right-click the stage you want to delete. The context menu is displayed.
- From the context menu, select Delete Stage. The confirmation dialog is displayed.
- In the confirmation dialog, click OK. The stage is deleted along with all steps.
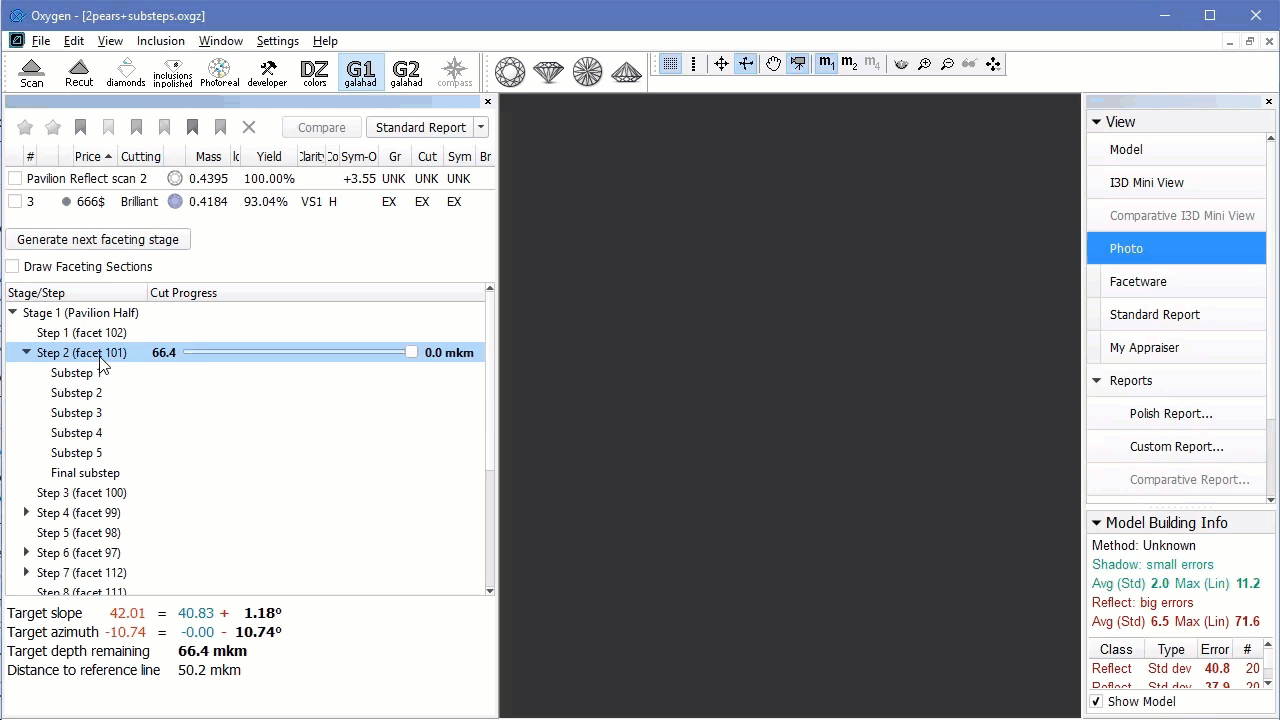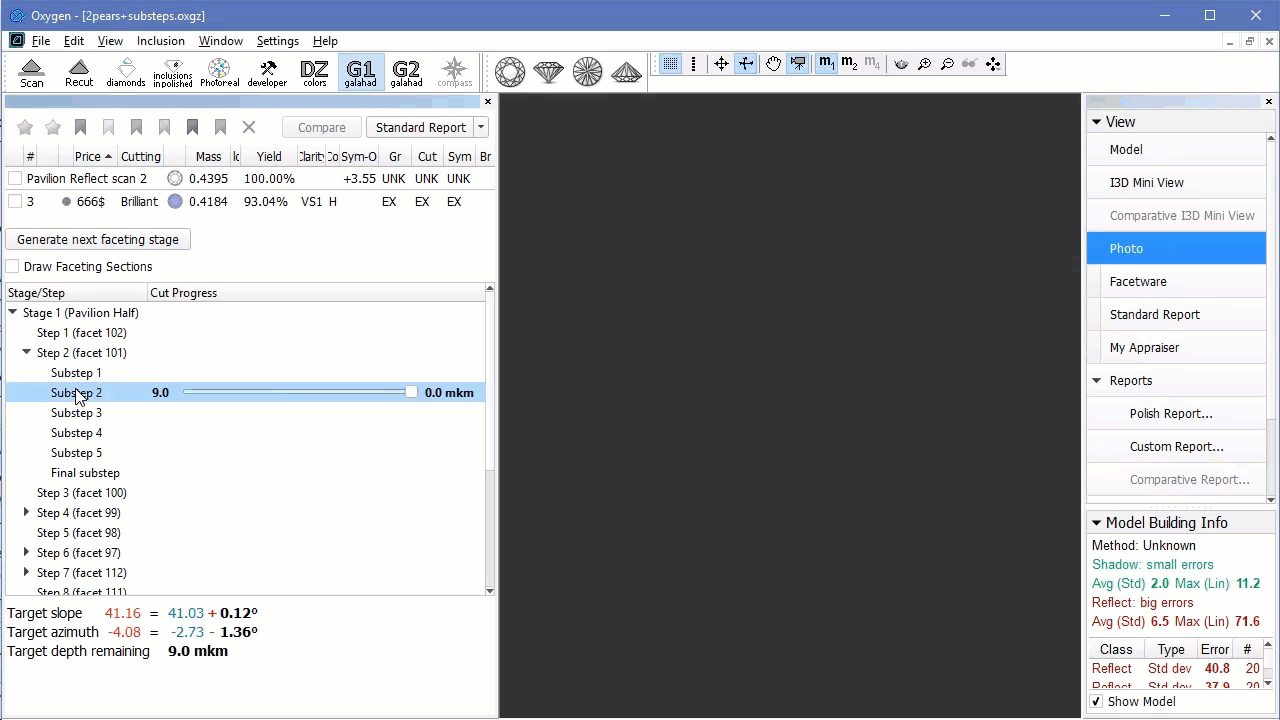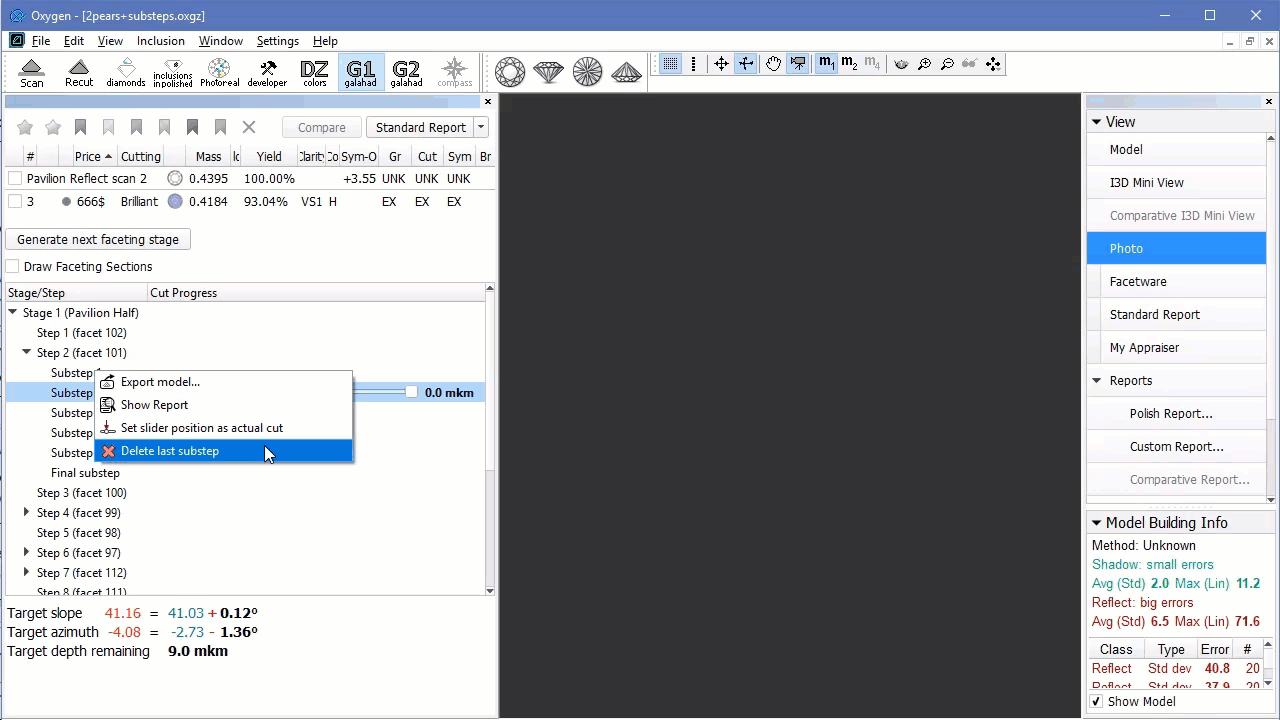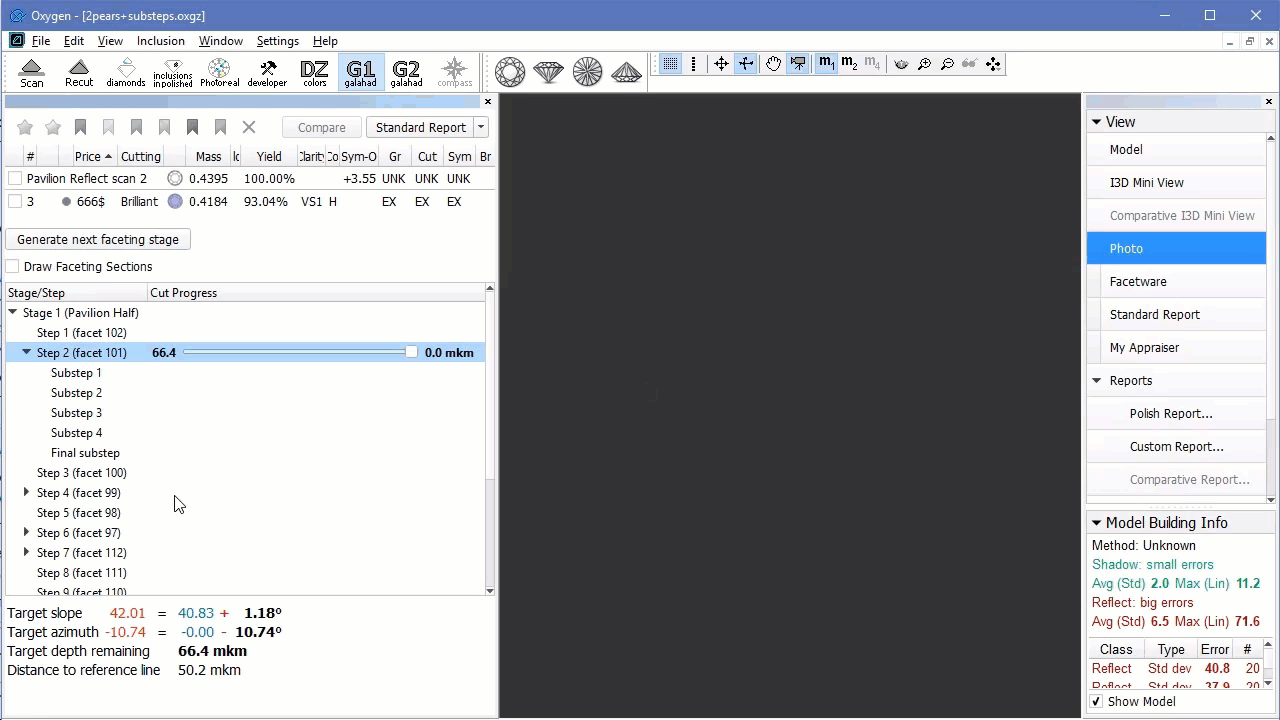
Deleting Last Sub-Steps of Steps
You can delete the last sub-step of the step. To do so:
- In the G1 Galahad mode, on the left panel do one of the following:
- Right-click the step for which you want to delete the last sub-step.
- Right-click any sub-step within the step for which you want to delete the last sub-step.
- From the context menu, select Delete last substep. The confirmation dialog is displayed.
In the confirmation dialog, click OK. The last sub-step of the current step is deleted.
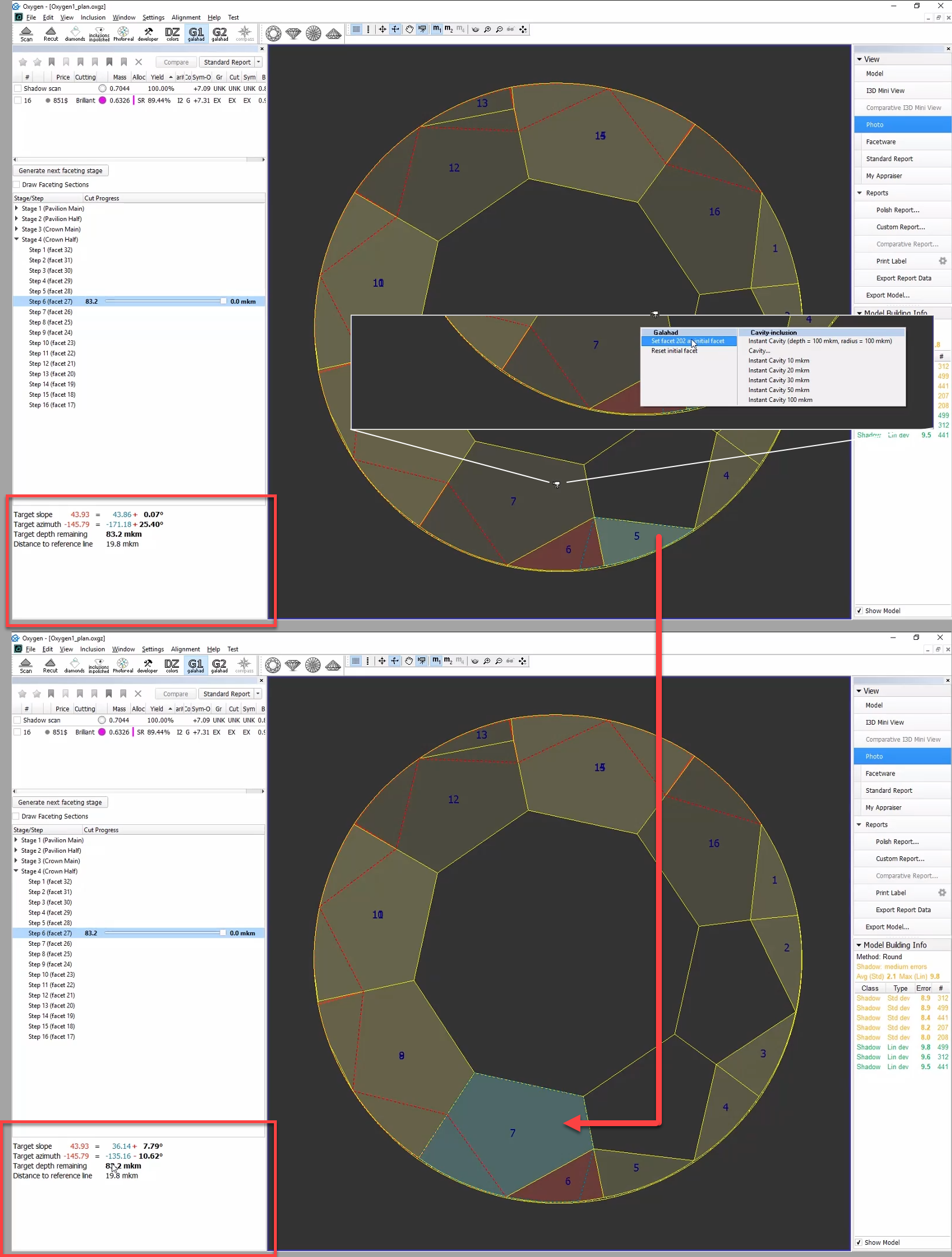
Manual Selection of Initial Facet
In Galahad Mode, for the selected step it is now possible to manually select the initial facet different from the one automatically calculated by the system. Once manually set, the initial facet can then at any moment be reset to the default one.
Related Pages
There is no content with the specified labels


1 Comment
Anonymous
The Invisible Character Copy Paste Phenomenon: Exploring its Uses and Implications
In the vast landscape of digital communication, where every character and symbol plays a role in conveying meaning, the concept of invisible character copy paste emerges as a fascinating yet often overlooked aspect of online interaction. Invisible characters, also known as zero-width characters or non-printing characters, are elements of text that lack a visible representation but can still influence the formatting, presentation, and interpretation of digital content. The ability to copy and paste these invisible characters has led to various applications and implications across different digital platforms and communication channels. This article aims to delve into the intricacies of invisible character copy paste, exploring its uses, impacts, and evolving significance in the modern era of communication of invisible symbol.
Understanding Invisible Characters and Copy Paste
Invisible characters are elements of text that are not displayed when rendered but still occupy space within the text stream. These characters include zero-width spaces, non-breaking spaces, zero-width joiners, and other control characters that are not visible to the naked eye but can affect the layout, formatting, and behavior of text. While they may not be apparent when viewing text, invisible characters can be copied and pasted like any other character, allowing users to manipulate and control the presentation of digital content.
The ability to copy and paste invisible characters has both practical and creative applications in digital communication. For instance, in document formatting and typesetting, invisible characters can be used to control line breaks, spacing, and alignment, ensuring that text is displayed in a visually appealing and readable manner. Similarly, in programming and web development, invisible characters are often employed to delimit strings, format code, or represent special characters that cannot be typed directly from the keyboard.
Creative Uses in Text Styling and Decoration
In addition to their practical applications, invisible character copy paste has given rise to creative uses in text styling and decoration, particularly in social media, messaging apps, and online forums. Users often employ invisible characters to add decorative elements, such as borders, dividers, or emphasis, to their text-based content, enhancing its visual appeal and expressiveness. For example, by inserting invisible characters before and after text segments, users can create the illusion of floating or suspended text, adding a whimsical or surreal touch to their messages.
Furthermore, invisible characters are frequently used in text-based games, puzzles, and riddles, where they serve as clues, hints, or hidden messages for players to decipher. By strategically embedding invisible characters within blocks of text, game designers can challenge players' observation skills and critical thinking abilities, enriching the gaming experience with layers of mystery and intrigue.
Privacy and Security Implications
While invisible character copy paste can be a fun and creative tool for digital expression, it also raises concerns about privacy and security, particularly in the context of social media, online messaging, and digital collaboration platforms. Malicious actors may exploit the ability to insert invisible characters into usernames, URLs, or messages to obfuscate malicious links, impersonate legitimate users, or evade content moderation algorithms. This can lead to various forms of online abuse, such as phishing attacks, spamming, or identity theft, posing risks to user safety and trust.
Additionally, invisible characters can be used in social engineering attacks, where attackers manipulate the appearance of text to deceive users into revealing sensitive information or performing malicious actions. For example, by disguising phishing URLs with invisible characters, attackers may trick users into clicking on fraudulent links that lead to malicious websites designed to steal login credentials or install malware on their devices.
Mitigating Risks and Promoting Awareness
To mitigate the risks associated with invisible character copy paste, digital platforms and communication tools must implement robust security measures and educate users about potential threats. This includes implementing content filtering algorithms to detect and block malicious uses of invisible characters, providing user-friendly reporting mechanisms for flagging suspicious content, and raising awareness about common social engineering tactics and phishing scams.
Moreover, users should exercise caution when interacting with text-based content online, particularly when clicking on links, sharing personal information, or engaging in conversations with unknown individuals. By remaining vigilant and skeptical of unusual or suspicious messages, users can protect themselves against various forms of online manipulation and deception.
invisible character copy paste represents a fascinating intersection of practical utility, creative expression, and security vulnerability in digital communication. From its uses in document formatting and code styling to its creative applications in social media and gaming, invisible characters play a diverse and multifaceted role in shaping the way we interact with digital content. However, it is essential to be mindful of the potential risks and implications associated with invisible character copy paste, particularly in terms of privacy, security, and online safety. By promoting awareness, implementing effective safeguards, and fostering responsible digital citizenship, we can harness the transformative power of invisible characters while mitigating the risks of abuse and exploitation in the digital realm."
Add Comment